Telegram spoilers are vulnerable and can be decoded 😳
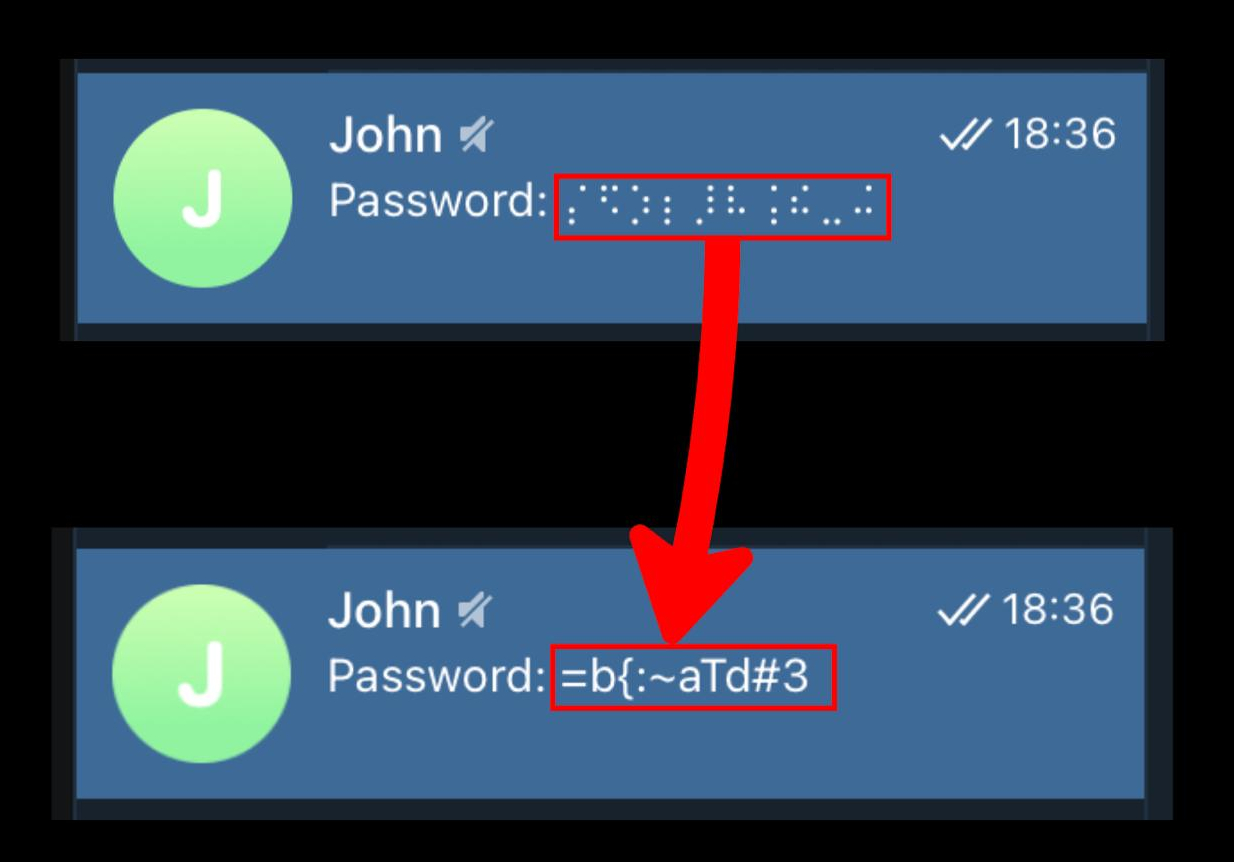
If you've ever shared your Telegram screen and used spoilers to hide certain info, I got bad news: your hidden text might be stolen.
The problem? Usually a spoiler is shown as an animated noise and only revealed on tap. But in some parts of the MacOS Telegram client it works differently, e.g. last message in the chat list and pinned message use a fallback that turns text into pseudo-Braille characters with a one-way mapping. The code: https://github.com/overtake/TelegramSwift/blob/579cebbf0c01fd41b712eff3647fa7f69db9665d/Telegram-Mac/Extensions.swift#L1805
This transform is mathematically non-invertible, but in practice we usually know the language and roughly what symbols someone uses. So you can guess and recover the original text with a limited brute-force over likely characters. 😨
Proof-of-concept encoder/decoder: https://github.com/rawrdcore/tg-hidden-messages-decoder
Huge thanks to @dalmatrix for researching and documenting https://t.me/rawrdcore/74 the privacy issue.
P.S. If you've ever put passwords or other secrets under a Telegram spoiler, now is a good time to change them! 😈